Supplier Cybersecurity
Information for Bell Suppliers on Cybersecurity Requirements
Where to start
The Defense Industrial Base is facing new threats every day. The Department of Defense needs its supply chain to enhance its resiliency in the cybersecurity space. Bell will provide information and tools to our subcontractors in efforts to secure the supply chain.
Understanding the Requirements
Use resources provided by several federal agencies to educate your business on the growing cybersecurity requirements.
Cyber Questionnaire
As a supplement to Bell's Annual Certification, the Cyber Questionnaire includes questions regarding your compliance to DFARS clause 252.204-7012 and your organization's cyber posture.
Incident Reporting
Suppliers who discover or suspect the occurrence of a cyber incident at their organization should report the incident to Bell.
Steps to cybersecurity maturity
Step 1: Exploring Cybersecurity Resources
Bell has created a Cybersecurity Resource Center to help our subcontractors build their compliance to regulatory requirements such as NIST 800-171 and the Cybersecurity Maturity Model Certification (CMMC). Please review the resources provided by several federal agencies dedicated to cybersecurity education. These resources provide affordable training courses, assessment tools, and specialists to help small businesses meet increasing contractual and regulatory requirements.
Project Spectrum: Created by the Office of Small Business Programs of the Department of Defense. The goal of Project Spectrum is to educate businesses about CMMC and how to be compliant. It includes training videos, webinars from DoD officials, online course, NIST Self-Assessment Tool, and more. See CMMC specific resources here.
NIST Small Business Cybersecurity Corner: Created by the U.S. Department of Commerce. This site provides cybersecurity basics, guidance, solutions, and training to protect your information and manage your risks. Look into The National Initiative for Cybersecurity Education (NICE) framework to access provides free and low-cost online cybersecurity training.
ND-ISAC CyberAssist: The DIB SCC Industry Task Force is identifying and posting links to helpful publicly available cybersecurity resources. The resources were selected both to help companies (i) meet DoD and other U.S. cybersecurity standards applicable to U.S. federal contractors (e.g., FAR Basic Safeguarding clause, DFARS Safeguarding CDI clause, CMMC); and (ii) otherwise improve their current cybersecurity protections.
Manufacturing Extension Partnership (MEP): The MEP Program is a national network with hundreds of specialists who understand the needs of America's small manufacturers. Contact your local MEP Center to learn how they can help you assess your business’s current risk posture, identify any gaps, and implement solutions to cost effectively protect your digital and information assets and meet your legal and contractual cybersecurity and privacy requirements.
DCSA CUI Resources: DCSA Program Office identified tools and resources to assist with the development of a successful CUI program for DOD and Industry.
CIO DIB Cybersecurity Program: The DoD DC3 team has compiled a list of no-cost Cybersecurity as-a-Service resources to reduce barriers to DIB community compliance and support contract cybersecurity efforts.
Step 2: Assessing Your NIST SP 800-171 Compliance
After reviewing the educational material, the subcontractors can create a System Security Plan (SSP) and a Plan of Action and Milestones (POA&M). These documents are necessary to document the implementation of NIST Special Publication 800-171, the publication called out in DFARS 252.204-7012 (Safeguarding Covered Defense Information and Cyber Incident Reporting).
The NIST SP 800-171 publication provides agencies with recommended security requirements for protecting the confidentiality of CUI. The requirements apply to all components of nonfederal systems and organizations that process, store, and/or transmit CUI, or that provide protection for such components. Click here to access the publication. Bell suppliers are required to attest their organization’s compliance to DFARS 252.204-7012 and indicate that the organization has enacted the security requirements in NIST SP 800-171 in section 10 of the Annual Certification.
NOTE: See Class Deviation 2024-O0013 for 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting, which requires contractors, who are subject to 252.204-712, to comply with NIST SP 800-171 Revision 2, instead of the version of NIST 800-171 in effect at the time the solicitation is issued or as authorized by the contracting officer. This class deviation is authorized by the contracting officer.
In addition to DFARS 252.204-7012, The Department of Defense has introduced two additional Defense Federal Acquisition Regulation Supplement (DFARS) requirements related to NIST SP 800-171.
| DFARS 252.204-7019 | DFARS 252.204-7020 |
|---|---|
| Notice of NIST SP 800-171 DoD Assessment Requirements |
NIST SP 800-171 DoD Assessment Requirements |
| Advises offerors required to implement the NIST SP 800-171 standards of the requirement to have a current NIST SP 800-171 DoD Assessment on record to be considered for award. Requires offerors to post current Assessments in the Supplier Performance Risk System (SPRS). | Requires contractors to provide the Government with access to its facilities, systems, and personnel when necessary for DoD to conduct or renew a higher-level NIST SP 800-171 DoD Assessment. |
The clauses above do not duplicate, overlap, or conflict with any other Federal rules. Rather these rules validate and verify contractor compliance with the existing cybersecurity requirements in FAR 52.204-21 and DFARS 252.204-7012 and ensures that the entire DIB sector has the appropriate cybersecurity processes and practices in place to properly protect FCI and CUI during performance of DoD contracts. Subcontractors need to complete the NIST SP 800-171 basic assessment and submit their results into the Supplier Performance Risk System (SPRS). This assessment methodology measures a company's compliance to the 110 controls of NIST SP 800-171. A NIST score could be zero, a negative score, or a perfect score being 110.
Step 3: Assessing Your CMMC 2.0 Compliance
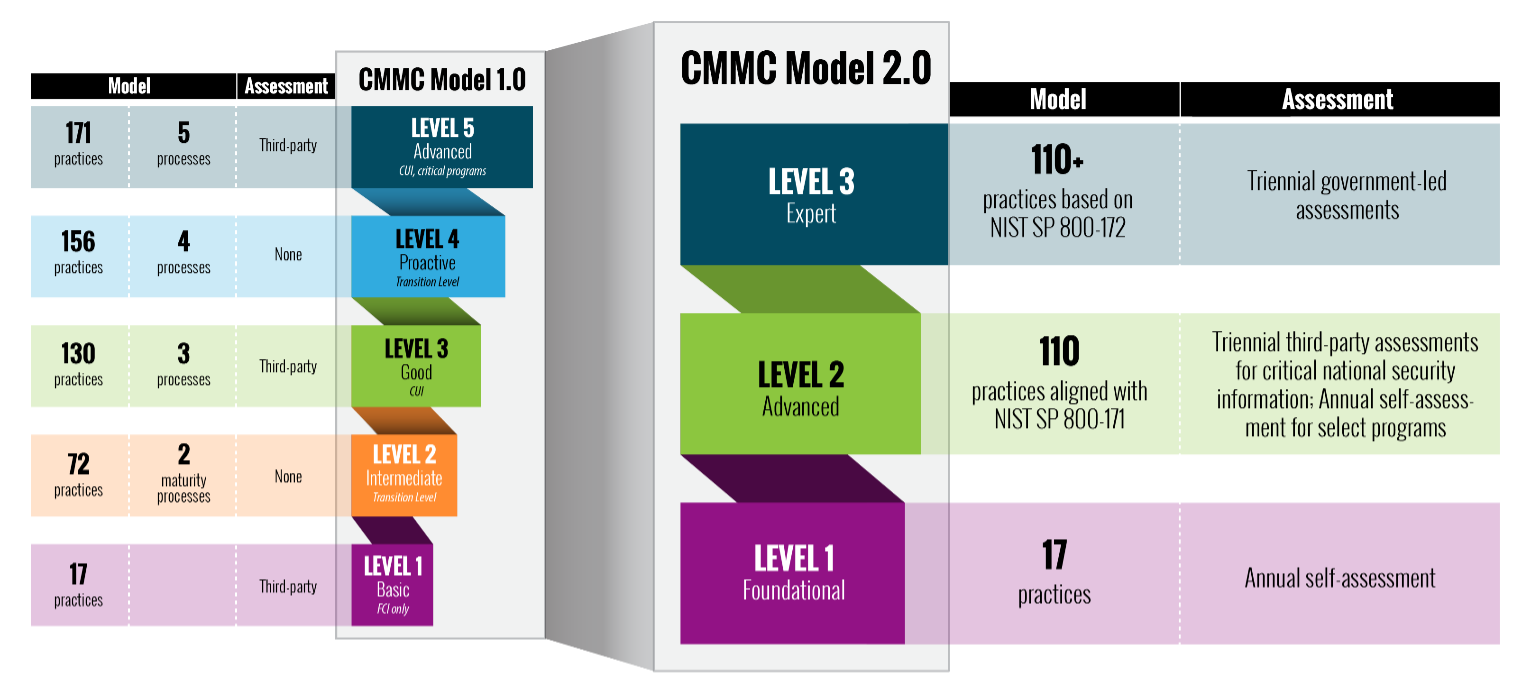
With the implementation of Cybersecurity Maturity Model Certification (CMMC) 2.0, the Department of Defense is introducing several key changes that build on and refine the original program requirements.
Streamlined Model
- Focused on the most critical requirements: Streamlines the model from 5 to 3 compliance levels
- Aligned with widely accepted standards: Uses National Institute of Standards and Technology (NIST) cybersecurity standards
Reduced Assessment Costs
- Reduced assessment costs: Allows all companies at Level 1 (Foundational) to demonstrate compliance through self-assessments
- Higher accountability: Increases oversight of professional and ethical standards of third-party assessors
Flexible Implementation
- Spirit of collaboration: Allows companies, under certain limited circumstances, to make Plans of Action & Milestones (POA&Ms) to achieve certification
- Added flexibility and speed: Allows waivers to CMMC requirements under certain limited circumstances
For updates on CMMC 2.0, visit https://dodcio.defense.gov/CMMC/.
We've made physical safety and quality a foundation in how we do business. Now it's time to do the same with our supply base by adopting and standardizing cybersecurity practices to protect the information in the DIB. CMMC builds upon DFARS 252.204-7012 (Safeguarding Covered Defense Information and Cyber Incident Reporting), which appears as a flow down in past DoD contracts.
Think of CMMC like a quality certification, and view the parallels below:
| AS9100 Rev D | CMMC | |
|---|---|---|
| Certification to do businesses with the DoD | Yes | Yes |
| Individual auditors | Yes | Yes |
| Renewable Certification | Yes | Yes |
| Goal of the Certification | Create a standard for Quality Management Systems in the Aviation, Space and Defense (AS&D) industry | Create a standard for cybersecurity practices and hygiene in the Defense Industrial Base (DIB). |
I don’t do business directly with the DoD, why does this apply to me?
Since CMMC is a DFARS requirement, it is mandated to be flowed down to the supply chain. Whether you're a 1st or 7th tier subcontractor, a CMMC level must be awarded for you in order to do business with the DoD at any level. The goal of CMMC is to mitigate risk of information theft at all levels.
Step 4: Crafting a Cybersecurity Plan for Your Business
1. Identify your Stakeholders
- Who will lead the CMMC initiative for the business?
- Who will be affected by this new requirement?
- Who will help interpret and implement changes that this requirement will bring in the business?
- Who will approve additional personnel/equipment needed to be CMMC compliant?
- Ex: Legal, Compliance, IT, Cybersecurity, Engineering, Procurement, Contracts
2. Quantify Resources and Personnel
- Should the business hire consultants or does the business have the resources and expertise to do a self-evaluation and implementation?
- How many man hours will be needed to be compliant?
- How much will I spend on software, hardware, or firmware purchases and upgrades to be compliant?
2. Determining the Right CMMC Level for your Business
- Who should help gauge my data sharing environment?
- Do I handle CUI or do I anticipate handling CUI in the future?
- How much data and what type of data from the prime do I access?
- How much data from the prime am I flowing down?
Cybersecurity Questionnaire
As a supplement to Bell's Annual Certification, the Cyber Questionnaire includes 13 questions regarding your compliance to regulatory requirements and your organization's cyber posture. The questionnaire consists of questions regarding:
- FAR 52.204-21 | Basic Safeguarding of Covered Contractor Information Systems.
- DFARS 252.204-7012 | Safeguarding Covered Defense Information and Cyber Incident Reporting.
- NIST SP 800-171 | Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations
- DFARS 252.204-7019 | Notice of NIST SP 800-171 DoD Assessment Requirements.
- IT Resources and Trainings
The questionnaire is located in your organization's ARIBA profile. Bell asks that the organization's IT team use their expertise to complete the information requested. If your organization is not subject to DoD regulatory requirements, please answer the questionnaire to the best of your abilities.
Subcontractor Cybersecurity Incident Reporting
In accordance with DFARS 252.204-7012, subcontractors must report cyber incidents to the DoD at https://dibnet.dod.mil within 72 hours of discovery.
After fulfilling reporting obligations to the DoD, subcontractors should provide the incident report number, assigned by DoD, to Bell as soon as practicable.
In addition to DIBNET reports, subcontractors should notify Bell of the following cybersecurity events:
- Any compromise of Information Technology systems, to include disruption of service, unauthorized access or transfer of information pertaining to existing contracts and goods provided to Bell.
- Any unauthorized changes to software, firmware or electronic components provided to Bell.
- Any claims by adversaries or security researchers of vulnerabilities or exploits affecting goods provided by the subcontractor.
These notifications should occur within 72 hours of discovery and made by email to scmcyberrisk@bellflight.com. The subcontractor shall provide additional information to Bell as requested.
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
CUI is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.
A CUI Registry provides information on the specific categories and subcategories of information that the Executive branch protects. The CUI Registry can be found at: https://www.archives.gov/cui. Resources, including online training to better understand CUI, can be found on National Archives’ website at https://www.archives.gov/cui/training.html.
For guidance on how to mark CUI data in your business, please review the training publication provided by the Department of Defense at https://www.dodcui.mil/Home/Desktop-Aids/.
How do I enter my NIST SP 800-171 Basic Assessment into SPRS?
To create a SPRS account, go to the Procurement Integrated Enterprise Environment (PIEE) Getting Started Page. To troubleshoot problems you may encounter when creating a PIEE account, please contact the PIEE Help Desk. Per the new provision DFARS 252.204-7019, offerors must ensure the results of any applicable current Assessments are posted in Supplier Performance Risk System (SPRS). Please review the Quick Entry Guide for step by step instructions to log your assessment into the Assessment Database. To troubleshoot problems you may encounter when entering your assessment, please review the FAQs or contact customer support.
What is the relationship between National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 and CMMC?
Under CMMC 2.0, the "Advanced" level (Level 2) will be equivalent to the NIST SP 800-171. The "Expert" level (Level 3), which is currently under development, will be based on a subset of NIST SP 800-172 requirements.
Additional questions?
Implementing and complying to growing cybersecurity regulations can be a challenge. For questions or additional information, please email scmcyberrisk@bellflight.com.
Topics of Discussion can include:
- NIST SP 800-171
- Cybersecurity Maturity Model Certification
- Roadblocks/Hurdles